Cracking WPA/WPA2 WPA Key Wireless Access Point Passphrase
In this article we will learn how to brute force a WPS key using
Airodump-ng, Reaver with Pixie Dust addon if your running an older
version of reaver update before starting this tutorial.
WPA/WPA2 (Wi-Fi Protected Setup) is impelled by most manufactures to secure routers & other wireless devices.
A
Wireless Interface in Modern Terms is a Wi-Fi adaptor or device that
connects to a Wireless Access Point. Today I will Show you how to bypass
the encryption in WPA/WPA2 Routers using a popular distro called Kali
Linux the reason I choice Kali Linux for this tutorial is that it comes
pre-installed with all the application that you will need it was
specially designed for Pen testers to test the security of their
networks and network devices it has a very wide range of applications we
will be using a select few of these applications we will be using
airodump-ng, reaver, pixiedust-wps (The name sounds cute but don’t let
that fool you.) I would properly put these applications in with the most
dangerous applications in cyber space the tool was created by Dominque
Bongard.
What
is WPS? WPS Stands for Wi-Fi Protected Setup WPS usually has a physical
push button on the front of your router to allow internet devices such
as Phones, iPods, iPads, Laptops Etc. to connect without ever entering
the wireless passphrase. There are 100,000,000 Possible Key Values
although the ending digit of the key value is known as a checksum witch
is calculated based on the last 7 digits lowering the process down to
10,000,000 possibilities. WPS breaks the Pins/Keys in half during this
process the keys are then broken down to 10,000 values for the first
half and 1,000 for the second half of the key-chain this totals 11,000
possible pins to try lowing the overall time of this process
drastically.
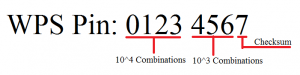
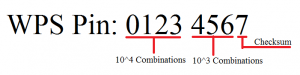
Now let’s get started to perform this attack you will need to open a new terminal within Kali Linux. Type in the terminal:
(where wlan0 is wireless interface name this command will put the wireless interface down.)
ifconfig wlan0 down
(where wlan0 is wireless interface name this command will put the wireless interface down.)
Now put your card into monitor mode using the command below.
This will allow your wireless interface to be placed in monitor mode.)
(This will then put your wireless interface back up in monitor mode.)
iwconfig wlan0 mode monitor
ifconfig wlan0 up
You can also use macchanger to change the physical mac address of your hardware Using such commands as
macchanger -r wlan0
(This will add random mac address to wireless interface make sure to take interface down and then back up once command is executed. Now your wireless card is in monitor mode lets scan for some Wireless signals. Open a terminal and type: airodump-ng wlan0 this will start the wireless scanning process all wireless networks including banned channels will be available.
Now you see all the info you will need on the wireless networks in question open a new terminal and type.
reaver -i wlan0 -b -c -vv
reaver -i wlan0 -b 00:11:22:33:44:55 -c 11 -vv
This will then start the process of brute forcing through the possible 11,000 Pins we talked about earlier. What is PixieDust-WPS and why use it? Well the name may sound cute and harmless don’t let this fool you this is a very powerful program. Some AP’s (Access Points) have weak E-S1 & E-S2 Encryptions that are meant to stay hidden if we can calculate this we can easily access WPA/WPA2 Pins of an access point.
E1
& E2 are gathered from M1 & M2 Package messages transmitted
through the air. Routers most vulnerable to this sort of attack include
Broadcom, Realtek, Ralink, Mediatek & Atheros to prevent this attack
you must turn WPS off in routers advanced configuration if router is
not compatible with the pixie dust attack mode switch to traditional
method.
Pixie
dust can crack a wireless access points WPS pin in less than 1 minute
usually on the first attempt of attack it will recover the WPS pin
traditional method could take 1 up to several hours you can see if your
router is vulnerable by typing this command in your command Terminal
reaver -i wlan0 -b -c -vvv -K1 -f
This
will perform this attack using the pixie dust WPS options shortly after
you will be greeted with the wireless pass phrase in my case I managed
to crack the password in 1 second proof of concept below.
These
methods are much quicker than the classic wordlists methods as a
wordlist containing so many million passphrases could take a very long
time to scan through. Once a hacker gains access to your local network
the possibilities of further attacks are endless.
Enjoy Hacking Vision will not be held reasonable for what the reader may do with this information.





