Get Anyone's Wi-Fi Password Without Cracking Using Wifiphisher
Do you need to get a Wi-Fi password but don't have the time to crack it? In previous tutorials, I have shown how to crack WEP, WPA2, and WPS,
but some people have complained that cracking WPA2 takes too long and
that not all access points have WPS enabled (even though quite a few
do). To help out in these situations, I present to you an almost
surefire way to get a Wi-Fi password without cracking—Wifiphisher.
Steps in the Wifiphisher Strategy
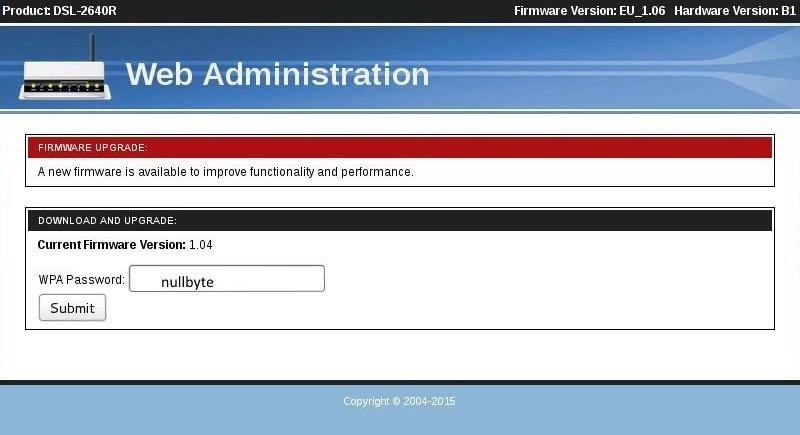
The idea here is to create an evil twin AP, then de-authenticate or DoS the user from their real AP. When they re-authenticate to your fake AP with the same SSID, they will see a legitimate-looking webpage that requests their password because of a "firmware upgrade." When they provide their password, you capture it and then allow them to use the evil twin as their AP, so they don't suspect a thing. Brilliant!To sum up, Wifiphisher takes the following steps:
- De-authenticate the user from their legitimate AP.
- Allow the user to authenticate to your evil twin.
- Offer a webpage to the user on a proxy that notifies them that a "firmware upgrade" has taken place, and that they need to authenticate again.
- The Wi-Fi password is passed to the hacker and the user continues to the web oblivious to what just happened.
To do this hack, you will need Kali Linux and two wireless adapters, one of which must be capable of packet injection. Here, I used the tried and true, Alfa AWUS036H. You may use others, but before you do, make certain that it is compatible with Aircrack-ng (packet injection capable). Please do NOT post questions on why it doesn't work until you check if your wireless adapter can do packet injection. Most cannot.
Now let's take a look at Wifiphisher.
Step 1Download Wifiphisher
To begin, fire up Kali and open a terminal. Then download Wifiphisher from GitHub and unpack the code.
kali > tar -xvzf /root/wifiphisher-1.1.tar.gz
As you can see below, I have unpacked the Wifiphisher source code.
When listing the contents of that directory, you will see that the wifiphisher.py script is there.
kali > ls -l

Step 3Run the Script
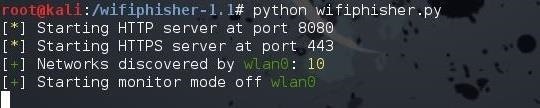
You can run the Wifiphisher script by typing:kali > python wifiphisher.py
Note that I preceded the script with the name of the interpreter, python.


kali > python wifiphisher.py
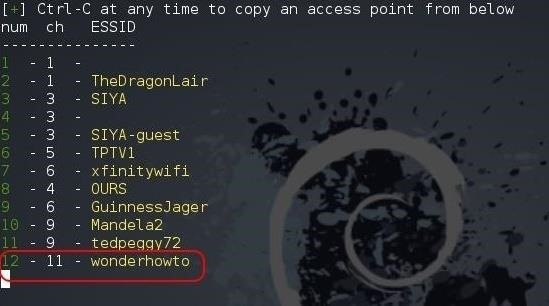
This time, it will start the web server on port 8080 and 443, then go about and discover the available Wi-Fi networks.
Step 4Send Your Attack & Get the Password
Go ahead and hit Ctrl + C on your keyboard and you will be prompted for the number of the AP that you would like to attack. In my case, it is 12.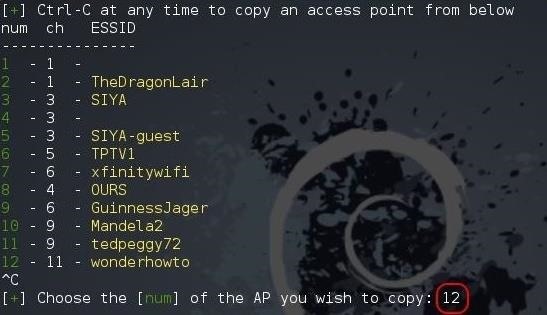
When they do, the proxy on the web server will catch their request and serve up an authentic-looking message that a firmware upgrade has taken place on their router and they must re-authenticate.